Yahoo Oauth Looks Like Something Went Wrong. Please Try Again Later.
The OAuth-based Google Sign-in "Streamlined" linking type adds Google Sign-In on top of OAuth-based account linking. This provides seamless voice-based linking for Google users while also enabling account linking for users who registered to your service with a non-Google identity.
This linking type begins with Google Sign-In, which allows you to bank check if the user'south Google profile information exists in your system. If the user's information isn't found in your arrangement, a standard OAuth flow begins. The user tin also choose to create a new account with their Google profile information.
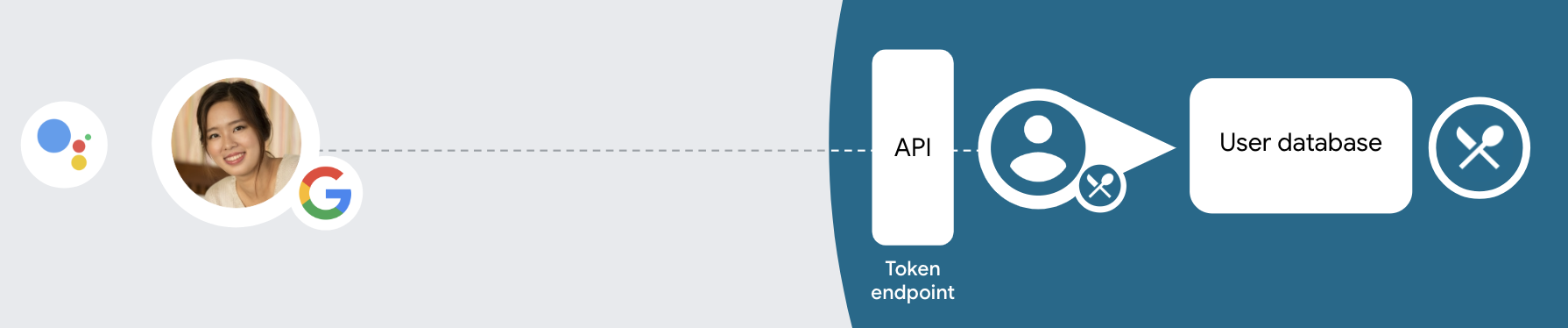
To perform account linking with the Streamlined linking type, follow these general steps:
- First, ask the user to give consent to access their Google profile.
- Use the information in their profile to identify the user.
- If you can't find a match for the Google user in your authentication system, the flow proceeds depending on whether you configured your Deportment project in the Actions console to allow user account creation via voice or but on your website.
- If y'all allow business relationship creation via voice, validate the ID token received from Google. Yous tin can so create a user based on the profile information contained in the ID token.
- If you don't allow business relationship creation via vocalisation, the user is transferred to a browser where they can load your say-so page and complete the user creation flow.
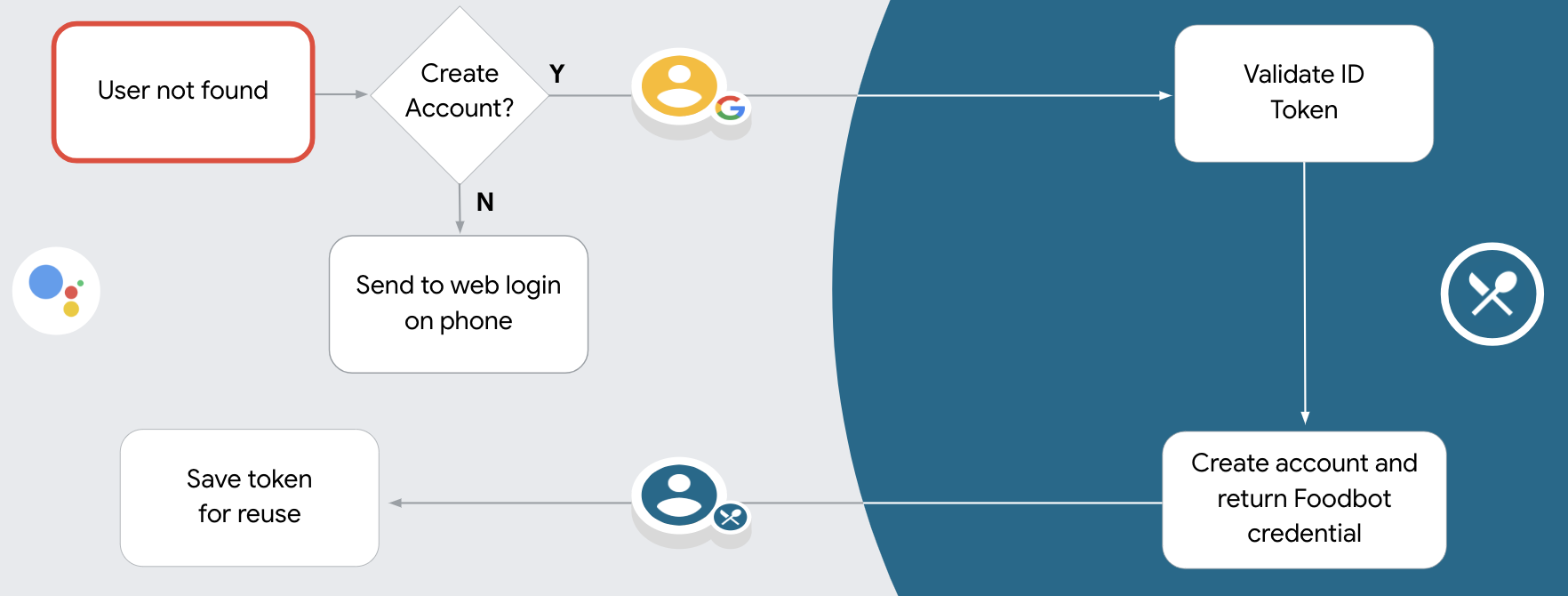
Support account creation via voice
If yous allow user business relationship cosmos via vocalisation, Banana asks the user whether they desire to practise the following:
- Create a new account on your system using their Google account information, or
- Sign in to your authentication system with a different business relationship if they take an existing not-Google account.
Allowing account creation via vocalism is recommended if you desire to minimize the friction of the account cosmos flow. The user only needs to leave the vox menstruum if they want to sign in using an existing non-Google account.
Disallow account cosmos via voice
If you disallowed user account creation via voice, Assistant opens the URL to the web site that you provided for user authentication. If the interaction is happening on a device that doesn't have a screen, Assistant directs the user to a phone to proceed the account linking flow.
Disallowing creation is recommended if:
-
You lot practice not want to allow users that accept non-Google accounts to create a new user business relationship and want them to link to their existing user accounts in your hallmark system instead. For example, if you offer a loyalty plan, y'all might want to make sure that the user doesn't lose the points accrued on their existing account.
-
Y'all need to have full control of the account creation flow. For example, you could disallow creation if you need to bear witness your terms of service to the user during account cosmos.
Implement OAuth-based Google Sign-in "Streamlined" linking
Accounts are linked with industry standard OAuth ii.0 flows. Actions on Google supports the implicit and authorization code flows.
In the implicit code menstruum, Google opens your say-so endpoint in the user's browser. Later on successful sign in, you return a long-lived access token to Google. This access token is now included in every request sent from the Assistant to your Action.
In the say-so code flow, you lot need two endpoints:
- The say-so endpoint, which is responsible for presenting the sign-in UI to your users that aren't already signed in and recording consent to the requested access in the class of a short-lived authority code.
- The token exchange endpoint, which is responsible for 2 types of exchanges:
- Exchanges an authorization lawmaking for a long-lived refresh token and a short-lived access token. This commutation happens when the user goes through the account linking flow.
- Exchanges a long-lived refresh token for a short-lived admission token. This exchange happens when Google needs a new admission token because the one it had expired.
Although the implicit code catamenia is simpler to implement, Google recommends that access tokens issued using the implicit flow never expire, because using token expiration with the implicit flow forces the user to link their account over again. If you need token expiration for security reasons, you should strongly consider using the auth code flow instead.
Configure the projection
To configure your projection to use Streamlined linking, follow these steps:
- Open the Actions console and select the project you desire to apply.
- Click on the Develop tab and choose Account linking.
- Enable the switch side by side to Account linking.
- In the Account cosmos section, select Yeah.
-
In Linking blazon, select OAuth & Google Sign In and Implicit.
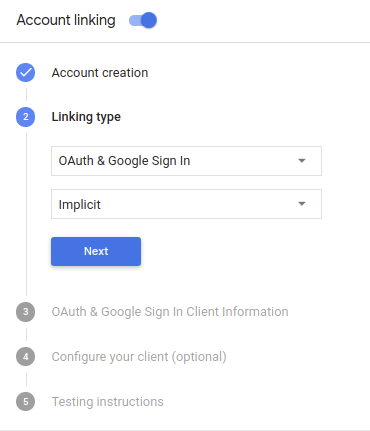
-
In Customer Data, do the post-obit:
- Assign a value to Client ID issued by your Actions to Google to identify requests coming from Google.
- Insert the URLs for your Authorization and Token Substitution endpoints.
-
Click Save.
Implement your OAuth server
To support the OAuth 2.0 implicit flow, your service makes an authorization endpoint bachelor past HTTPS. This endpoint is responsible for authenticating and obtaining consent from users for data access. The authorization endpoint presents a sign-in UI to your users that aren't already signed in and records consent to the requested access.
When your Action needs to call 1 of your service's authorized APIs, Google uses this endpoint to get permission from your users to call these APIs on their behalf.
A typical OAuth ii.0 implicit menstruum session initiated by Google has the post-obit menstruum:
- Google opens your authorization endpoint in the user'south browser. The user signs in if non signed in already, and grants Google permission to access their data with your API if they haven't already granted permission.
- Your service creates an access token and returns it to Google by redirecting the user'southward browser back to Google with the access token attached to the request.
- Google calls your service'southward APIs, and attaches the access token with each request. Your service verifies that the admission token grants Google authorization to access the API and then completes the API call.
When your Action needs to perform account linking via an OAuth 2.0 implicit menstruation, Google sends the user to your potency endpoint with a request that includes the following parameters:
| Authorization endpoint parameters | |
|---|---|
client_id | The client ID you lot assigned to Google. |
redirect_uri | The URL to which you send the response to this asking. |
state | A bookkeeping value that is passed back to Google unchanged in the redirect URI. |
response_type | The blazon of value to render in the response. For the OAuth ii.0 implicit period, the response type is always token. |
For example, if your authorisation endpoint is bachelor at https://myservice.example.com/auth, a request might wait like:
GET https://myservice.instance.com/auth?client_id=GOOGLE_CLIENT_ID&redirect_uri=REDIRECT_URI&country=STATE_STRING&response_type=token
For your potency endpoint to handle sign-in requests, do the following steps:
-
Verify the
client_idandredirect_urivalues to forbid granting access to unintended or misconfigured client apps:- Ostend that the
client_idmatches the client ID yous assigned to Google. - Confirm that the URL specified by the
redirect_uriparameter has the following form:https://oauth-redirect.googleusercontent.com/r/YOUR_PROJECT_ID
YOUR_PROJECT_ID is the ID found on the Project settings page of the Actions Panel.
- Ostend that the
-
Bank check if the user is signed in to your service. If the user isn't signed in, complete your service'southward sign-in or sign-up menstruum.
-
Generate an access token that Google will utilize to access your API. The access token tin can exist any string value, but it must uniquely correspond the user and the client the token is for and must not be guessable.
-
Send an HTTP response that redirects the user'south browser to the URL specified by the
redirect_uriparameter. Include all of the post-obit parameters in the URL fragment:-
access_token: the access token you just generated -
token_type: the stringbearer -
state: the unmodified state value from the original asking The post-obit is an case of the resulting URL:https://oauth-redirect.googleusercontent.com/r/YOUR_PROJECT_ID#access_token=ACCESS_TOKEN&token_type=bearer&country=STATE_STRING
-
Google's OAuth 2.0 redirect handler will receive the access token and ostend that the state value hasn't changed. Subsequently Google has obtained an access token for your service, Google will attach the token to subsequent calls to your Action equally part of the AppRequest.
Handle automatic linking
Later on the user gives your Action consent to access their Google profile, Google sends a asking that contains a signed assertion of the Google user'southward identity. The assertion contains information that includes the user's Google Account ID, name, and e-mail address. The token exchange endpoint configured for your projection handles that asking.
If the corresponding Google business relationship is already present in your authentication system, your token commutation endpoint returns a token for the user. If the Google account doesn't match an existing user, your token commutation endpoint returns a user_not_found error.
The request has the post-obit form:
Mail service /token HTTP/i.1 Host: oauth2.instance.com Content-Blazon: application/x-world wide web-class-urlencoded grant_type=urn:ietf:params:oauth:grant-blazon:jwt-bearer&intent=get&assertion=JWT&consent_code=CONSENT_CODE&scope=SCOPES
Your token exchange endpoint must be able to handle the following parameters:
| Token endpoint parameters | |
|---|---|
grant_type | The type of token being exchanged. For these requests, this parameter has the value urn:ietf:params:oauth:grant-type:jwt-bearer. |
intent | For these requests, the value of this parameter is `get`. |
assertion | A JSON Spider web Token (JWT) that provides a signed assertion of the Google user'due south identity. The JWT contains information that includes the user's Google Account ID, name, and email address. |
consent_code | Optional: When present, a 1-fourth dimension lawmaking that indicates that the user has granted consent for your Action to access the specified scopes. |
scope | Optional: Whatsoever scopes you configured Google to request from users. |
When your token exchange endpoint receives the linking request, information technology should do the following:
Validate and decode the JWT assertion
You lot tin can validate and decode the JWT assertion by using a JWT-decoding library for your linguistic communication. Use Google's public keys (available in JWK or PEM format) to verify the token's signature.
When decoded, the JWT exclamation looks like the following instance:
{ "sub": 1234567890, // The unique ID of the user'south Google Account "iss": "https://accounts.google.com", // The assertion's issuer "aud": "123-abc.apps.googleusercontent.com", // Your server's client ID "iat": 233366400, // Unix timestamp of the assertion's cosmos time "exp": 233370000, // Unix timestamp of the exclamation's expiration time "proper name": "January Jansen", "given_name": "January", "family_name": "Jansen", "electronic mail": "jan@gmail.com", // If present, the user's electronic mail address "locale": "en_US" } In add-on to verifying the token's signature, verify that the assertion's issuer (iss field) is https://accounts.google.com and that the audience (aud field) is the client ID assigned to your Activeness.
Check if the Google account is already present in your authentication system
Bank check whether either of the following conditions are true:
- The Google Business relationship ID, plant in the assertion'southward
subfield, is in your user database. - The email address in the assertion matches a user in your user database.
If either condition is true, the user has already signed upwardly and you tin can effect an access token.
If neither the Google Account ID nor the electronic mail address specified in the exclamation matches a user in your database, the user hasn't signed up even so. In this instance, your token exchange endpoint should reply with a HTTP 401 error, that specifies fault=user_not_found, every bit in the following example:
HTTP/1.i 401 Unauthorized Content-Blazon: application/json;charset=UTF-viii { "error":"user_not_found", } When Google receives the 401 error response with a user_not_found error, Google calls your token exchange endpoint with the value of the intent parameter set to create and sending an ID token that contains the user's contour data with the request.
Handle account creation via Google Sign-In
When a user needs to create an account on your service, Google makes a request to your token exchange endpoint that specifies intent=create, as in the post-obit example:
Postal service /token HTTP/ane.1 Host: oauth2.example.com Content-Type: awarding/x-www-form-urlencoded response_type=token&grant_type=urn:ietf:params:oauth:grant-type:jwt-bearer&scope=SCOPES&intent=create&consent_code=CONSENT_CODE&assertion=JWT[&NEW_ACCOUNT_INFO]
The assertion parameter contains A JSON Web Token (JWT) that provides a signed assertion of the Google user's identity. The JWT contains information that includes the user's Google Account ID, proper name, and electronic mail address, which you can utilise to create a new account on your service.
To answer to business relationship creation requests, your token commutation endpoint must do the following:
Validate and decode the JWT exclamation
You tin validate and decode the JWT assertion past using a JWT-decoding library for your language. Use Google's public keys (available in JWK or PEM format) to verify the token's signature.
When decoded, the JWT assertion looks like the following example:
{ "sub": 1234567890, // The unique ID of the user'due south Google Account "iss": "https://accounts.google.com", // The assertion's issuer "aud": "123-abc.apps.googleusercontent.com", // Your server's client ID "iat": 233366400, // Unix timestamp of the exclamation's creation time "exp": 233370000, // Unix timestamp of the assertion'south expiration time "name": "Jan Jansen", "given_name": "January", "family_name": "Jansen", "email": "jan@gmail.com", // If nowadays, the user's electronic mail address "locale": "en_US" } In add-on to verifying the token's signature, verify that the assertion'due south issuer (iss field) is https://accounts.google.com and that the audience (aud field) is the client ID assigned to your Action.
Validate user information and create new account
Check whether either of the following weather condition are true:
- The Google Business relationship ID, found in the assertion'due south
subfield, is in your user database. - The electronic mail address in the assertion matches a user in your user database.
If either status is true, prompt the user to link their existing account with their Google Business relationship by responding to the request with an HTTP 401 error, specifying error=linking_error and the user's email address as the login_hint, equally in the following example:
HTTP/1.one 401 Unauthorized Content-Blazon: application/json;charset=UTF-eight { "fault":"linking_error", "login_hint":"foo@bar.com" } If neither condition is true, create a new user account using the data provided in the JWT. New accounts do non typically have a password set. It is recommended that you add together Google Sign In to other platforms to enable users to log in via Google across the surfaces of your awarding. Alternatively, you can email the user a link that starts your password recovery flow to allow the user to fix a countersign for signing in on other platforms.
When the creation is completed, issue an access token and return the values in a JSON object in the trunk of your HTTPS response, like in the following example:
{ "token_type": "Bearer", "access_token": "ACCESS_TOKEN", "expires_in": SECONDS_TO_EXPIRATION } Design the voice user interface for the authentication flow
Check if the user is verified and start the business relationship linking flow
- Open your Actions Builder projection in the Actions Console.
- Create a new scene to start business relationship linking in your Activeness:
- Click Scenes.
- Click the add (+) icon to add together a new scene.
- In the newly created scene, click the add icon for Conditions.
- Add a condition that checks if the user associated with the conversation is a a verified user. If the bank check fails, your Activity tin't perform account linking during the chat, and should fall back to providing access to functionality that doesn't require account linking.
- In the
Enter new expressionfield under Status, enter the post-obit logic:user.verificationStatus != "VERIFIED" - Under Transition, select a scene that doesn't require account linking or a scene that is the entry bespeak to guest-only functionality.
- In the
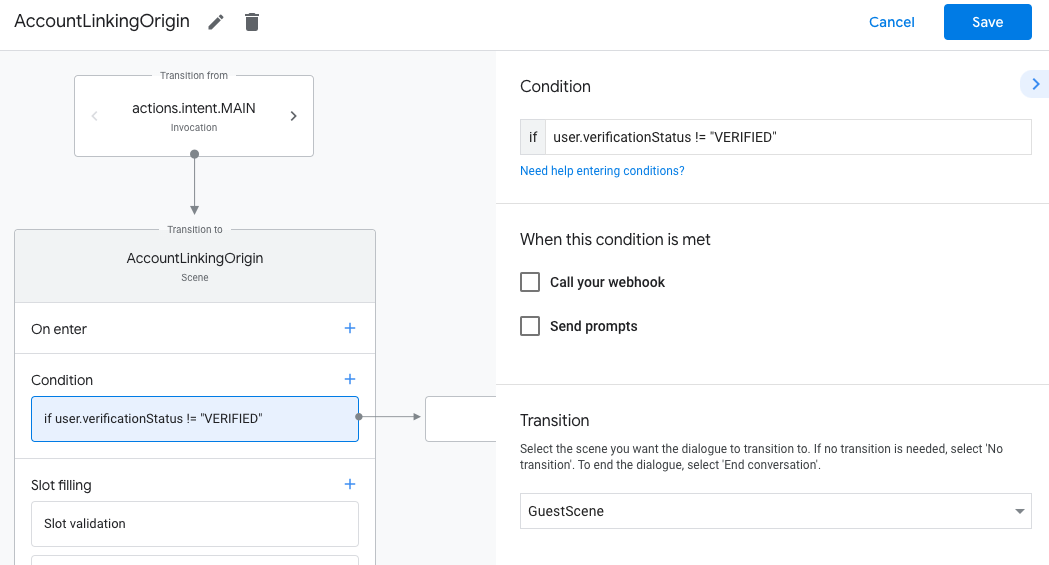
- Click the add icon for Conditions.
- Add a condition to trigger an account linking flow if the user doesn't have an associated identity.
- In the
Enter new expressionfield nether Condition, enter the following logic::user.verificationStatus == "VERIFIED" - Under Transition, select the Business relationship Linking system scene.
- Click Salve.
- In the

After saving, a new account linking arrangement scene called <SceneName>_AccountLinking is added to your projection.
Customize the account linking scene
- Nether Scenes, select the account linking system scene.
- Click Send prompt and add a curt sentence to depict to the user why the Action needs to admission their identity (for example "To save your preferences").
- Click Salve.
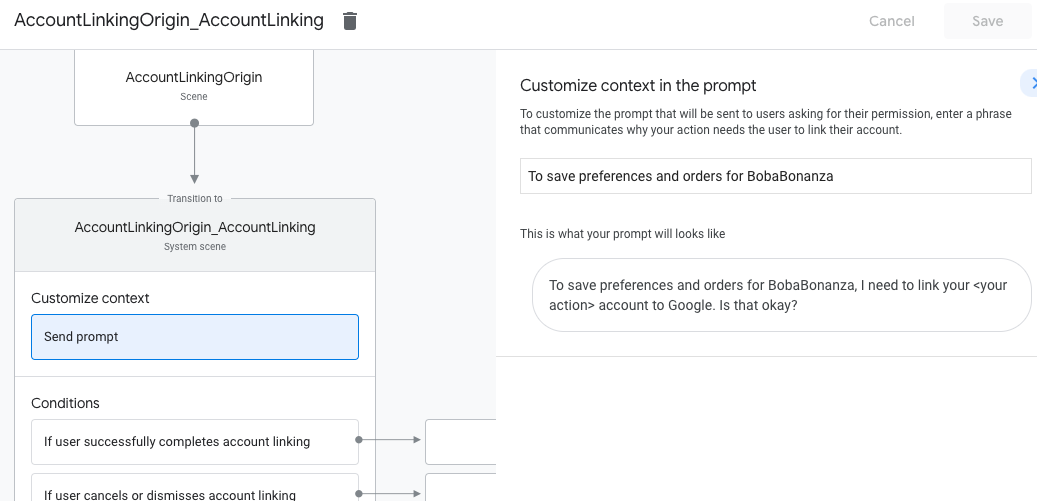
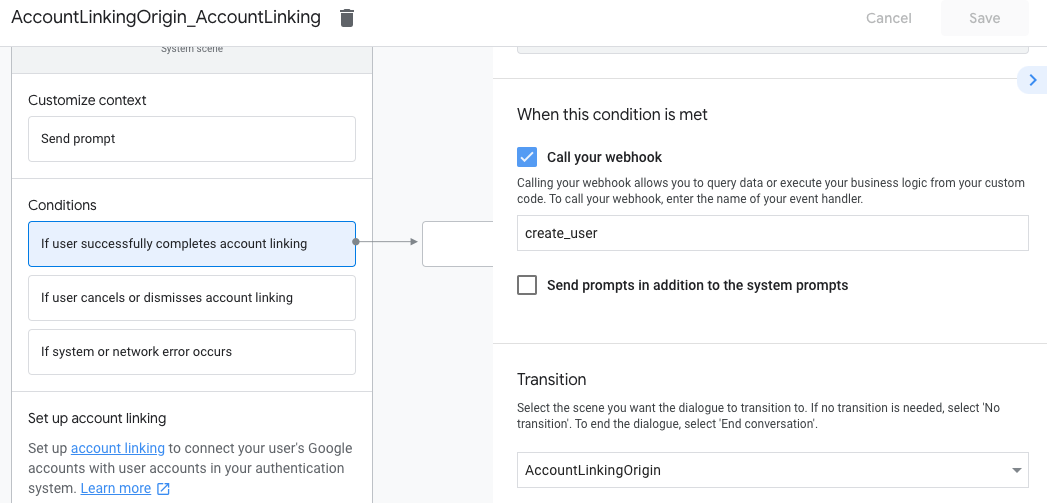
- Under Conditions, click If user successfully completes account linking.
- Configure how the flow should proceed if the user agrees to link their account. For example, call the webhook to procedure any custom business organization logic required and transition back to the originating scene.
- Click Save.
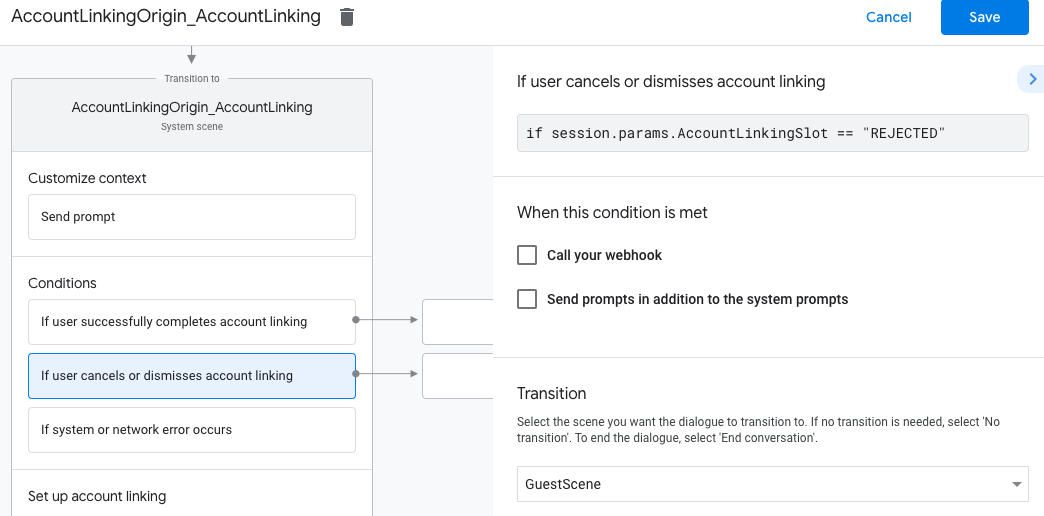
- Under Conditions, click If user cancels or dismisses account linking.
- Configure how the menstruum should continue if the user doesn't agree to link their account. For example, send an acknowledging message and redirect to scenes that provide functionality that doesn't require business relationship linking.
- Click Save.
- Under Weather condition, click If arrangement or network fault occurs.
- Configure how the flow should go along if the business relationship linking flow can't be completed considering of system or network errors. For instance, ship an acknowledging message and redirect to scenes that provide functionality that doesn't require account linking.
- Click Save.
Handle information admission requests
If the Assistant request contains an admission token, check kickoff that the admission token is valid and non expired and so retrieve from your user account database the user account associated with the token.
shewmakerdecterral.blogspot.com
Source: https://developers.google.com/assistant/identity/google-sign-in-oauth
0 Response to "Yahoo Oauth Looks Like Something Went Wrong. Please Try Again Later."
Post a Comment